Research Article Open Access
Study of Wireless Mesh Network over Medium Access Control Layer
Meenu Talwar1* and Sandeep Singh Kang21M.Tech (CSE), Department of Computer Science and Engineering, C.G.C, Punjab Technical University, Jalandhar, India
2Associate Prof, Department of Computer Science and Engineering, C.G.C, Punjab Technical University, Jalandhar, India
- *Corresponding Author:
- Meenu Talwar
M.Tech (CSE), Department of Computer Science and Engineering, C.G.C
Punjab Technical University, Jalandhar, India
Email: er.meenutalwar@gmail.com
Visit for more related articles at International Journal of Advance Innovations, Thoughts & Ideas
Abstract
Ad hoc networks can be established every time and everywhere, and they are usually comprised of a group of workstations or other wireless devices that communicate directly with each other to exchange information. Usually there is no central management available. The topology in ad hoc networks may change rapidly due to the unpredictable mobility of individual devices. A wireless mesh network (WMN) come under the category of Ad hoc networks that is a collection of self-configuring, self-healing stationary mesh routers and mobile clients. In the dissertation deploy multiple applications in the WMN scenario that was not done in the previous research work and also to provide Internet in the network scenario used in this report. TCP Reno protocol has been used to improve the performance of symmetric networks. This protocol providing end to end link connection maintained on the network devices. It tries to detect impending congestion by tracking the average queue size in the recent past and then informs the receiver to dynamically decrease the frequency of acks so that each ack effectively acknowledges several packets. From the proposed work, first analyze the benefits of asymmetric links and second perform a simulation study in which measure the performance of the Network scenario. All experimental results are based on OPNET base simulator implementation. We also implement a model especially designed asymmetric networks that is used to monitor network conditions and gather relevant metrics and factor values. Experimental results show that the proposed modeling technique is able to overcome the problems like Response time and throughput.
Keywords
Ad hoc network, Wireless network, TCP Reno protocol, asymmetric link, WMN
Introduction
A WMN consists of several nodes interconnected via wireless links (possibly employing multiple radio interfaces) and exploiting multi-hop communications in order to deliver data services to the end-users. With respect to conventional star-shaped networks, WMNs offer advantages in terms of enhanced robustness (in that no single points of failure are present and redundant links are encompassed) and flexibility (without the need for deploying cables, connectivity may be provided only where and when needed/economically attractive). Likewise, WMNs differ from the ad hoc paradigm since the network is not anymore made of a homogeneous set of devices, on the opposite, nodes involved in the communication can play two different logical roles, i.e., mesh clients or mesh routers. Mesh clients are the end-users’ devices that dynamically join/leave the network, while mesh routers are in charge of forwarding packets to and from the wired infrastructure the WMN gives access to. The two media that have seen the widest use in local-area applications are infrared light and radio waves. Most portable PCs sold now have infrared ports that can make quick connections to printers and other peripherals. However, infrared light has limitations; it is easily blocked by walls, partitions, and other office construction. Radio waves can penetrate most office obstructions and offer a wider coverage range. It is no surprise that most, if not all, 802.11 products on the market use the radio wave physical layer [17,12].
In order to turn WMNs into a commodity it is mandatory to develop techniques capable of enhancing the perceived end-user’s experience. As matter of fact, it is widely acknowledged that the next-generation Internet will be characterized by an extreme variety of multimedia broadband services. Unlike traditional “pure data” applications like FTP or HTTP, multimedia services impose strict requirements in terms of packet loss, latency, delay and jitter. Although WMNs can serve as a standalone communication systems for disaster recovery or public safety, this thesis focuses on access network applications. In this scenario, a distinction exists in terms of logical roles supported by the physical devices:
• Relay: building the multi-hop wireless backhaul by establishing links between a selected set of nodes.
• Gateway: interfacing the WMN with another network, typically the Internet.
• Access point: providing wireless connectivity to clients.
• Client: gaining network access for end users.
Technologies
In principle, WMNs could interface, through suitable gateway nodes, with networks based on different radio technologies (3G, WiFi, Bluetooth, wimax, etc.). However, most actual solutions, in both academic and business environments, heavily rely on the IEEE 802.11 family of standards.
IEEE 802.11 Protocol
IEEE 802.11s Task Group (TG) plans to integrate mesh networking services and protocols within 802.11MAC layer. The resulting systems will be compatible with the IEEE 802.11 Infrastructure Mode. In this standard, peer-to-peer L2 links among multiple IEEE 802.11s Mesh Points can be established to enable direct or multi-hop data delivery for higher throughput and range extension.
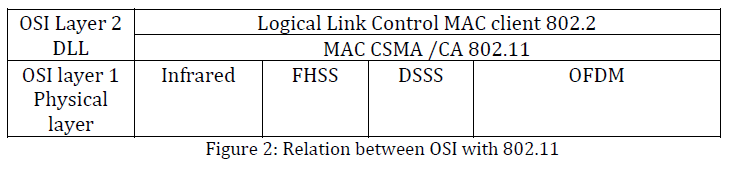
The 802.11 protocol specifies the nature of 802.11 frames and their transport over the Physical and Media Access Control sub layer of the Data Link layer using the Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA) protocol. The various 802.11x standards that were just described define the network access mechanisms and port assignments used by wireless devices to connect to Ethernet networks.[13] The placement of the different 802.11 standards in relation to the OSI networking model are shown in figure 2.
In this model, the MAC layer handles synchronization, power management, roaming, and the MAC-MIB. The Physical layer contains the Physical Layer Convergence Protocol (PLCP) and Physical Medium Dependent (PMD) sub layers. As you can see in Figure 1, there are several different modulation schemes in use in the Physical layer. These include FHSS, DSSS, and OFDM transmissions, which were described in the given below sections are:
Frequency Hopping Spread Spectrum (FHSS)
In The Frequency Hopping Spread Spectrum (FHSS) modulation bit rate for original IEEE802.11 standard is 2Mbps. And S band ISM (Individual Scientific and Medical) frequency band which operate in frequency range of 2.4 to 2.5 GHz.
Direct-Sequence Spread Spectrum (DSSS)
.The major enhancement to IEEE802.11 by IEEE 802.11b is standardization of physical layer to support higher bit rate. It support 2 additional speed such as 5.5 Mbps and 11Mbps using S band ISM.
Orthogonal Frequency Division Multiplexing (OFDM)
Orthogonal Frequency Division Multiplexing (OFDM) is digital frequency division technology that is used by 802.11a/g/n/y. In this technology, multiple subcarrier waves are overlaid on top of each other with an offset so that the peak of one subcarrier overlaps with the trough of another.
Routing
WMNs share a number of features with ad hoc networks [7]. In particular, WMNs are characterized by self-organization and self-healing capabilities and exploit multi-hopping to build a wireless backhaul for delivering Internet connectivity to end-users. As a result, many routing protocols developed for Mobile Ad hoc Networks (MANETs) have been adapted to fit the mesh environments.[18] Particular attention has been devoted to the introduction of novel routing metrics capable of achieving better performance in outdoor deployments by considering the wireless channel characteristics [8]. Routing can be either provided at level three of the ISO/OSI networking stack as modification of the standard IP protocol or by adding an interposition layer between the Data Link Layer and the Network layer In the latter solution the multi-hop backhaul is transparent to the upper networking stack making the WMN appear like a LAN. On the other hand, such an approach introduces additional encapsulation and processing overhead as a result respectively of the header and the checksum required by the interposition level. This implies a slight reduction in overall performance.
802.11 Architecture
802.11 is a member of the IEEE 802 family, which is a series of specifications for local area network (LAN) technologies.[1,2] In IEEE 802.11 the addressable unit is a station (STA), which is a message destination, but not a fixed location. IEEE 802.11 handles both mobile and portable stations [11]. Mobile Stations (MSs) access the LAN while in motion, whereas a Portable Station (PS) can be moved between locations, but it is used only at a fixed location.
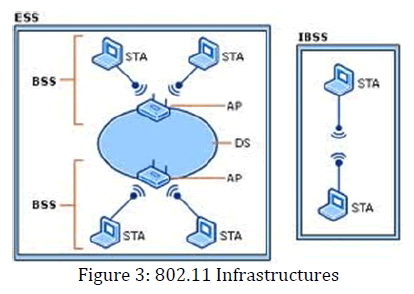
The IEEE 802.11 architecture provides a WLAN supporting station mobility transparently to upper layers. The Basic Service Set (BSS) is the basic building block consisting of member stations remaining in communication. If a station moves out of its BSS, it can no longer directly communicate with other members of the BSS [3]. A BSS may form the Distribution System (DS), which is an architectural component used to interconnect BSSs. IEEE 802.11 logically separates the Wireless Medium (WM) from the Distribution System Medium (DSM).
The DS and BSSs allow IEEE 802.11 to create a wireless network of arbitrary size and complexity called Extended Service Set (ESS) network. The ESS network appears the same to an LLC layer as an IBSS network. Stations within an ESS may communicate and MSs may move from one BSS to another (within the same ESS), transparently to LLC. A portal is the logical point at which MAC Service Data Units (MSDUs) from an integrated non-IEEE 802.11 LAN enter the IEEE 802.11 DS.
Architectural services of IEEE 802.11 are as follows: authentication, association, deauthentication, disassociation, distribution, integration, privacy, re-association, and MSDU delivery. These services are provided either by stations as the Station Service (SS) or by the DS as the Distribution System Service (DSS). Currently, the widespread use of IEEE 802.11 cards makes this technology the most interesting off-the-shelf enabler for ad hoc networks. However, the standardization efforts have concentrated on solutions for infrastructure-based WLANs, whereas little or no attention has been given to the ad hoc mode. Therefore, the aim of this theory is triple:
i. An in-depth investigation of the ad hoc features of the IEEE 802.11 standard,
ii. An analysis of the performance of 802.11-based ad hoc networks.
iii. An investigation of the major problems arising when using the 802.11 technology for ad hoc networks, and possible directions for enhancing this technology for a better support of the ad hoc networking paradigm.
Asymmetric Networks
In a wireless environment, at any given time, an asymmetric link supports unidirectional communication between a pair of mobile stations and requires a set of relay stations for the transmission of packets in the other direction. The term “asymmetric” is related to the transmission range of a node at time t and a communication channel linking two nodes. Two nodes linked by an asymmetric link at time t may find themselves in close proximity, or may be able to increase their transmission range and to reach each other at time (t+τ) and thus be connected by a bi-directional link. Thus to make a distinction between unidirectional and asymmetric links is in wireless networks.
Symmetric and asymmetric connections, connection-oriented and connectionless data transport, as well as variable bit rates up to 2.88 Mbit/s per carrier are supported by the standard [4,5]. Asymmetry Network is an important routing phenomenon, which can influence the manner in which, we model and simulate the Internet. For a pair of hosts A and B, if the path from A to B (forward direction) is different from the path from B to A (reverse direction), we say that the pair of paths between A and B exhibit routing asymmetry. This asymmetry can appear on both AS level and router level paths. Asymmetry at the AS level also leads to router level asymmetry. However, router level asymmetry can exist even if the AS paths are symmetric; this would be due to asymmetry within an AS.
Long term asymmetric routes are mainly created due to routing policies and traffic engineering. [5] A packet in a provider's network but destined for a different network, is moved out of the provider's network as per the provider's policies. This is done even if it would cause the packet to experience a longer path or higher levels of congestion than what exists within the provider's network.
MAC Layer
The design of MAC layer protocol assumes significance in an Asymmetric networks because achievable capacity depends heavily on the performance of MAC protocol. In addition to a fully distributed operation, the major issues faced by the popular CSMA/CA-based IEEE 802.11 distributed coordination function (DCF) is:
i. Hidden terminal problem
ii. Exposed terminal problem.
Therefore, new MAC protocols are to be designed for operating in multichannel systems. MAC protocols are also to be adapted to operate in different physical layer technologies such as UWB and MIMO physical layers. In traditional wireless or wired networks, each layer works with its own information making it unable to make the best use of the network-centric properties. In general, the MAC layer protocol design should include methods and solutions to provide better network scalability and throughput capacity [6,7].
Most traditional medium access protocols are designed for nodes with omnidirectional antennas and for sharing a single channel. Examples include Aloha, Slotted Aloha, carrier sense multiple access (CSMA), and CSMA with collision avoidance (CSMA/ CA). [8] The two MAC protocols defined in the IEEE 802.11 standards, i.e., the IEEE 802.11 MAC protocol and the IEEE 802.11e quality of service (QoS) enhancement MAC protocol, are single-channel MAC protocols designed for nodes with unidirectional antennas. [7]
IEEE 802.11e MAC Architecture
IEEE 802.11e MAC Protocol the IEEE 802.11e standard draft defines a number of QoS enhancements to IEEE 802.11. Two main functional blocks are defined in IEEE 802.11e:
i. The channel access functions and
ii. The traffic specification (TSPEC) management.
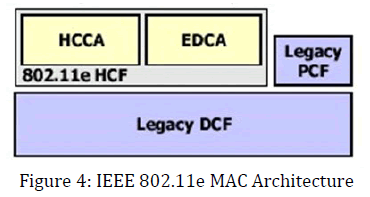
The channel access function defines a new coordination function called the hybrid coordination Function (HCF). [14] HCF has two modes of operation: a contention based protocol called enhanced distributed channel access (EDCA) and a polling mechanism called HCF controlled channel access (HCCA). Both access functions enhance or extend the functionalities of the original 802.11 access method, i.e., DCF, and operate on top of DCF (Figure 4). Because the operation of HCCA and PCF requires a central control entity and synchronization among nodes, they are hard, if not impossible, to realize in a WMN. Hence, we focus mainly on the EDCA access method. EDCA enhances the original DCF by providing prioritized medium access based on different traffic classes, also called access categories (ACs).
The IEEE 802.11e defines four ACs, each of which has its own queue and its own set of EDCA parameters. The differentiation in priority between ACs is realized by setting different values for the EDCA parameters [2].
MAC Management
Differences between the wireless network environment and the traditional wired environment create challenges for network protocol designers. This section examines a number of the hurdles that the 802.11 designers faced.
RF Link Quality
On a wired Ethernet, it is reasonable to transmit a frame and assume that the destination receives it correctly. Radio links are different, especially when the frequencies used are unlicensed ISM bands. Even narrowband transmissions are subject to noise and interference, but unlicensed devices must assume that interference will exist and work around it [15]. The designers of 802.11 considered ways to work around the radiation from microwave ovens and other RF sources. In addition to the noise, multipath fading may also lead to situations in which frames cannot be transmitted because a node moves into a dead spot. Unlike many other link layer protocols, 802.11 incorporate positive acknowledgments.
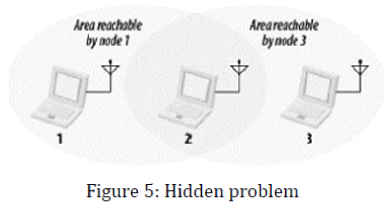
The Hidden Node Problem
In Ethernet networks, stations depend on the reception of transmissions to perform the carrier sensing functions of CSMA/CD. Wires in the physical medium contain the signals and distribute them to network nodes.[6] Wireless networks have fuzzier boundaries, sometimes to the point where each node may not be able to communicate with every other node in the wireless network.
In figure 5, node 2 can communicate with both nodes 1 and 3, but something prevents nodes 1 and 3 from communicating directly. (The obstacle itself is not relevant; it could be as simple as nodes 1 and 3 being as far away from 2 as possible, so the radio waves cannot reach the full distance from 1 to 3.) From the perspective of node 1, node 3 is a hidden node. If a simple transmit-and-pray protocol was used, it would be easy for node 1 and node 3 to transmit simultaneously, thus rendering node 2 unable to make sense of anything. Furthermore, nodes 1 and 3 would not have any indication of the error because the collision was local to node 2.
MAC Access Modes and Timing
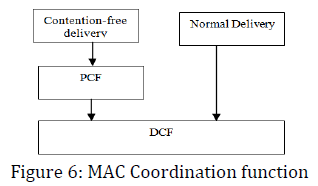
Access to the wireless medium is controlled by coordination functions. Ethernet-like CSMA/CA access is provided by the distributed coordination function (DCF). If contention-free service is required, it can be provided by the point coordination function (PCF), which is built on top of the DCF. Contention-free services are provided only in infrastructure networks. The coordination functions are described in the following list and illustrated in Figure 6.
DCF
The DCF is the basis of the standard CSMA/CA access mechanism. Like Ethernet, it first checks to see that the radio link is clear before transmitting [16]. To avoid collisions, stations use a random back off after each frame, with the first transmitter seizing the channel. In some circumstances, the DCF may use the CTS/RTS clearing technique to further reduce the possibility of collisions. Frame exchanges under the DCF dominate the 802.11 MAC. According to the rules of the DCF, all products are required to provide best-effort delivery. To implement the contention-based MAC, stations process MAC headers for every frame while they are active [9].
PCF
Point coordination provides contention-free services. Special stations called point coordinators are used to ensure that the medium is provided without contention. Point coordinators reside in access points, so the PCF is restricted to infrastructure networks. To gain priority over standard contention-based services, the PCF allows stations to transmit frames after a shorter interval.
Problem Formulation
With the advances of wireless communication technology, low-cost and powerful wireless transceivers are widely used in mobile applications. Wireless networks have attracted significant interest in recent years because of their improved flexibility and reduced costs. Compared to wired networks From the early work done in the Asymmetric networks for evaluating the performance of downstream and upward stream [5], and various Authors [1,10] extend this work by providing internet connectivity on the Asymmetric Networks. The Authors [3,4] also worked on homogeneous and heterogeneous ranges and avoiding broadcast problem and hidden station problems.
In this proposed work further extend the above problem by modeling the Asymmetric network in MAC layer and providing internet connectivity. The early work [3,4] used gateway and routers for providing internet connectivity but in this work used ATM (Asynchronous Transfer Mode) technology for providing virtual connectivity in between nodes and the server. The advantage of this technology over previous technology is that by using virtual connectivity the large number of nodes easily connected and transferring high quality of data without any interruption [8]. It also eliminates the looping problem by forcing all nodes in the network to participate in some form of intermodal coordination protocol. There are also some modification in the coding part that the packets may be transmitted containing either layer-2 (MAC) addresses or layer-3 (network) addresses. Routing information is advertised by broadcasting or multicasting the packets which are transmitted periodically and incrementally as topological changes are detected (e.g., when stations move within the network).
Methodology used
From the early work done in the Asymmetric networks for evaluating the performance of downstream and upward stream [5], and various Authors [1,10] extend this work by providing internet connectivity on the Asymmetric Networks. The Authors [3,4] also worked on homogeneous and heterogeneous ranges and avoiding broadcast problem and hidden station problems. In this proposed work further extend the above problem by modeling the Asymmetric network in MAC layer and providing internet connectivity. The early work [3,4] used gateway and routers for providing internet connectivity but in this work used ATM (Asynchronous Transfer Mode) technology for providing virtual connectivity in between nodes and the server. The advantage of this technology over previous technology is that by using virtual connectivity the large number of nodes easily connected and transferring high quality of data without any interruption.
Experimental Scenario Used
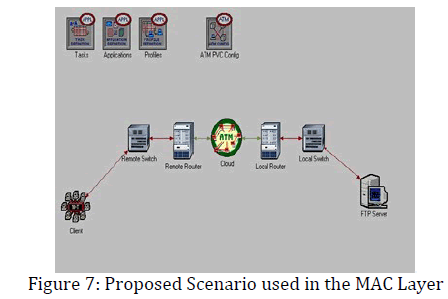
The proposed modeling technique has shown in figure 7. This scenario is represented by a small Ethernet (10BaseT_LAN). All the computers in this small Ethernet are connected with 10Mbps link. This Ethernet consists of twenty (10) workstations, one Ethernet server, and one switch. The use of an IP cloud is also necessary for providing internet to the two different LANS such as local as well as remote routers. Applications can be Database Access, E- mail, File Transfer, File Print, Telnet Session, Video Conferencing, Voice over IP call or Web Browsing. An application may be any of the common application (email, file transfer) or a custom application you define. A profile is applied to a workstation, server or LAN. It specifies the application used by a particular group of users. You might have one profile for marketing (heavy use of e- mail; light use of file transfer) and another profile for engineering (light use of e-mail; heavy use of file transfer). From the implementation point of view the scenario used in the above figure created by using Opnet and coding done on VC++ and some of the part of JAVA.
Conclusion & Future Work
In this work, we present our framework in OPNET simulator for asymmetry networks and apply it to real Internet measurements. Thus, we compute the distribution of the routing asymmetry in the Internet at both the local and remote link/router levels. Our MAC protocol used in the implementation reduces average packet loss ratio and average delay as asymmetric links are comprehensively utilized which dominate routing in heterogeneous ad hoc networks. In addition, a test network can be setup in the laboratory once the actual Asymmetric Network hardware and software have arrived and the network analysis tool can be installed into the Networks system to analyze the results. The test scenarios generated in this study could be reproduced and actual traffic data obtained from the tested can be used to compare with the OPNET analysis performed in this study. Further research should be conducted with more realistic representations of the target network by modeling the network using the models found in the OPNET WDM Guru.
References
- V. Paxson, “End to end behavior in the Internet”, In Proceeding of the ACM SIGCOMM, Volume 26, number 4, page 25-38, August 1996.
- Y. He, M. Faloutsos, S. V. Krishnamurthy, “Quantifying Routing Asymmetry in the Internet at the AS Level”, IEEE GLOBECOM 2004 – Global Internet and Next Generation Networks, Dallas, Texas, November, 2004.
- M.Murugesan, A. Krishnan, “Reliable and Efficient Algorithm for Broadcasting in Asymmetric Mobile Ad hoc Networks”, International Journal of Computer Applications, July 2010.
- Ashok Kumar. S, Krishnammal. N, “Addressing Asymmetric Link in Wireless Mesh Networks”, International Journal of Modern Engineering Research,2012.
- Balakrishnan H. and Venkata N., “How Network Asymmetry Affects TCP,” IEEE Communications Magazine, pp. 60-67, 2001.
- Shreedhar M. and Varghese G., “Efficient Fair Queueing Using Deficit Round-Robin”, IEEE/ACM Transcations on Networking, pp 375-385, 1996.
- V. Jacobson, “Congestion avoidance and control”, ACM SIGCOMM, Aug1998.
- S. Floyd, V. Jacobson, “Link-Sharing and Resource Management Models for Packet Networks”, IEEE/ACM Transactions on Networking, Vol3, No4, August 1995.
- S. Kumar, V. S. Raghavan, and J. Deng, “Medium access control protocols for ad hoc wireless networks: a survey,” Ad Hoc Networks Journal, Elsevier, vol. 4, pp. 326–358, 2006.
- He, Y., Faloutsos, M., Krishnamurthy, S. Huffaker, B, “ On routing asymmetry in the internet”, In: Proceedings of IEEE Globecom, 2005. (2005)
- D. Knuth. Pre-Fascicle, “The Art of Computer Programming”, Volume 4, Addison-Wesley.
- A. Howard, M. J. Mataric and G. S. Sukhatme, “Relaxation on a mesh: A formalism for generalized localization,” International Conference on Intelligent Robots and Systems (IROS), October 29 - November 3, Maui, IEEE 2001, pp. 1055-1060.
- S. Hedetniemi, A. Liestman, “A survey of gossiping and broadcasting in communication networks”, Networks 18 (4) (1988) pp.319–349.
- W. Heinzelman, “Application specific protocol architectures for wireless networks”, PhD Thesis, MIT, 2000.
- Y. B. Ko, V. Shankarkumar, N. H. Vaidya. “Medium Access Control Protocols Using Directional Antennas in Ad Hoc Networks,” in the Proceedings of the IEEE INFOCOM 2000 - Volume 1, Tel-Aviv Israel, March 2000, pp. 13-21.
- Mahesh K. Marina and Samir R. Das, ‘‘A topology control approach to channel assignment in multi-radio wireless mesh networks,’’ in 2nd International Conference on Broadband Networks (Broadnets), Boston, MA, October 2005.
- Arindam K. Das, Hamed M.K. Alazemi, Rajiv Vijayakumar, Sumit Roy, ‘‘Optimization Models for Fixed Channel Assignment in Wireless Mesh Networks with Multiple Radios,’’ Proceedings of Second Annual IEEE Communications Society Conference on Sensor and Ad Hoc Communications and Networks, 2005.
- Doina Bein,“Self-Configuring, Self-Organizing, and Self-Healing Schemes in Mobile Ad Hoc Networks”,Springer,2009.
Relevant Topics
- Advance Techniques in cancer treatments
- Advanced Techniques in Rehabilitation
- Artificial Intelligence
- Blockchain Technology
- Diabetes care
- Digital Transformation
- Innovations & Tends in Pharma
- Innovations in Diagnosis & Treatment
- Innovations in Immunology
- Innovations in Neuroscience
- Innovations in ophthalmology
- Life Science and Brain research
- Machine Learning
- New inventions & Patents
- Quantum Computing
Recommended Journals
Article Tools
Article Usage
- Total views: 18890
- [From(publication date):
January-2013 - Apr 03, 2025] - Breakdown by view type
- HTML page views : 14174
- PDF downloads : 4716