Research Article Open Access
Global Chemical, Biological, and Nuclear Threat Potential Prioritization Model
Susan Caskey1, Barry Ezell2*and Robin Dillon-Merrill3
1Sandia National Laboratories, USA
2Senior Principal Analyst, Innovative Decisions Inc, Vienna, VA 22182, USA
3Principal Analyst, Innovative Decisions Inc, USA
- *Corresponding Author:
- Barry Ezell, Ph.D.
Senior Principal Analyst
Innovative Decisions Inc
1945 Old Gallows Rd
Vienna, VA 22182, USA
Tel: 757-638-4439
E-mail: bezell@innovativedecisions.com
Received Date: September 10, 2013; Accepted Date: November 25, 2013; Published Date: November 28, 2013
Citation: Caskey S, Ezell B, Dillon-Merrill R (2013) Global Chemical, Biological, and Nuclear Threat Potential Prioritization Model. J Bioterr Biodef 4:125 doi: 10.4172/2157-2526.1000125
Copyright: © 2013 Caskey S, et al. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited.
Visit for more related articles at Journal of Bioterrorism & Biodefense
Abstract
The Global Chemical, Biological, and Nuclear Threat Potential model is designed to provide a systematic and defensible technical prioritization of countries based the relative threat potential of each country. Threat potential is defined as the potential for a non-state actor (or terrorist organization) to exploit resources from within the country that support the development of a weapon of mass destruction or effect. This is accomplished by assessing the potential for successful acquisition of materials, expertise, and equipment, which are needed in the building of a weapon; and, the presence of a terrorist organization or organizations in the country aiming to develop such a weapon.
Keywords
Nuclear threat; Prioritization
Introduction
Cooperative threat reduction programs endeavoring to reduce chemical, biological, and nuclear (CBN) threats should have a systematic and logical way to identify and prioritize country engagements. A process that can systematically and logically identify and prioritize country engagements provides a defensible rationale for country engagement, a foundation for strategic implementation of threat reduction measures in a country or region, and a metric to measure the impact of threat reduction activities.
Global CBN Threat Potential Prioritization (G-CBN-TP) model is designed to provide this systematic prioritization of countries based on the relative threat potential of each country. The goal of the G-CBN-TP model is to answer the following question: What is the relative potential for a non-state actor to exploit the infrastructure of a country with the intension of building a weapon of mass destruction or mass effect (WMD/WME)? To answer this question, the model has been designed to compare various countries based upon the vulnerabilities of their relevant infrastructures and the potential threat posed by non-state actors within them.
The non-state-actor threat and the infrastructure of a country are defined and uniquely modeled in three separate modules: global chemical threat potential prioritization model (GCTP), global biological threat potential prioritization model (GBTP), and global nuclear threat potential prioritization model (GNTP). The individual results of these modules can be used for independent decision analysis or combined to look for larger trends regarding global threats.
The technical threat potential captured within the G-CBN-TP is defined as a two-dimensional problem: the threat posed by a nonstate actor and the ability of a non-state actor to exploit the existing infrastructure of a country to develop a WMD/WME. The G-CBN-TP model is organized into a series of attributes, which define each of these dimensions.
Non-State-Actor Threat
The assessment of the threat from non-state actors within a country is based upon measuring the known or suspected capabilities and intensions of non-state actors and societal factors regarding a country’s overall vulnerability to non-state actors. The societal factors include the stability of the country, level of corruption, and economic equality.
The assessment of a non-state actor’s potential access to a country’s infrastructure is based upon assessing two attributes:
• The overall scale of the relevant infrastructure of a country compared to other countries; and
• The effectiveness and level of implemented security measures.
country’s infrastructure is measured by proxy data, which is used to define the extent of relevant academic programs, level of research and development, and extent of the relevant industries within the country.
Security effectiveness, implementation, and culture
The effectiveness and level of security implementation are measured by informed opinion of subject matter experts (SMEs) regarding implemented security and control measures and overall security culture. Security and control measures are defined as prevention and detection of and response to theft, sabotage, and unauthorized access, illegal transfer, or other malicious acts involving relevant material. It should be noted that security includes physical protection, personal reliability, material control and accountability, transportation security, information security, and program management. A security culture is the assembly of characteristics, attitudes and behavior of individuals, organizations and institutions, which serves as a means to support and enhance safety, security, and standard best practices. These practices include dual-use/responsible-use considerations. Several institutions and individuals are necessary for the development of an effective security culture: the state, organizations, and managers in organizations, personnel, the public, and the international community. A strong security culture should include domestic (government, organizations, and personnel) measures, as well as international engagement of best practices and technical/personnel assistance.
Methodology
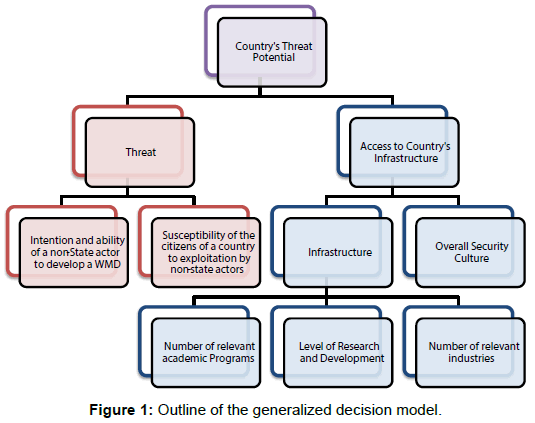
The G-CBN-TP model is based on a multiple-objective decision analysis (MODA) framework, shown in. In a MODA approach, the objectives are organized into a hierarchy of factors (for this application, threat and vulnerability factors) where the lowest-level objectives are quantified by measurable scoring [1]. MODA is used in decision analysis and risk analysis when problems have multiple objectives, often in conflict, that require quantifying explicit value tradeoffs. MODA integrates objective facts explicitly with value preference judgments. MODA models are well proven to help support policy decisions [2]. A MODA model is useful when the decision requires organizing and aggregating many variable and conflicting factors in a clear, transparent and accountable way. Additionally, the MODA approach allows for explicitly documenting when there is a limited amount of available data (e.g., availability of biological agents in a country) or when the measurement of data is problematic. Finally, the MODA approach provides a structured, consistent method for looking at and comparing abstract concepts (in this case, ‘threat’ and ‘vulnerability’), or concepts that can only be approximated due to the limited amount of available data [3] (Figure 1).
Threat is defined as the presence, intent, and capability of non-state actors within the country. Threat has two supporting objectives:
• Intention and ability of a non-state actor to develop a WMD is defined by using constructed scales, scored by subject matter experts.
• Susceptibility of the citizens of a country to exploitation by non-state actors is defined based upon several different country based stability and radicalization indices.
Access to Country’s Infrastructure is defined as access to CBN infrastructure (vulnerabilities) and has two supporting objectives:
• Infrastructure – defined by potential amount of materials, expertise and technologies; with three attribute measures:
• The number of relevant academic programs.
• The amount of relevant research and development.
• The number and level of production of relevant industries.
• Overall Security Culture – defined by compliance to international best practices and the level of implementation of security practices within institutions.
The G-CBN-TP model is a value model that explicitly analyzes alternatives on the basis of the defined objectives. The G-CBN-TP value model consists of four components: defining attributes that measure objectives to be used for evaluating countries, defining value functions for each attribute to convert each to a common scale, assessing weights for attributes when needed to aggregate different attributes into one overall score, and defining an algorithm for combining a country’s attribute scores with the weights to produce the overall relative value score. In the first component, objectives are defined in terms of measureable criteria or attributes [3], where these attribute must be understandable, measurable, non-redundant, and independent.
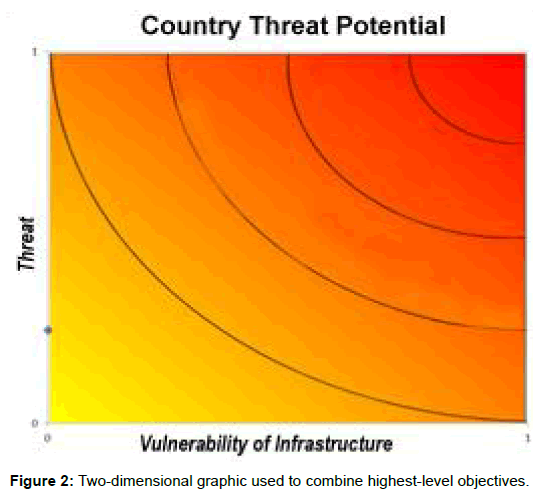
Some attributes are preferentially independent, which means that the preferences for one criterion do not depend on the scores for another criterion [4]. For those attributes that are independent, the attributes can be aggregated using a weighted additive function. For those attributes, which are judged to be interdependent, the G-CBNTP model either uses a two-dimensional value function to capture the combined attributes (Figure 2), two-dimensional graphic used to combine highest-level objectives, or it uses a multiplicative function to appropriately combine the two attributes and still capture the interdependency [5].
A value model converts each attribute measurement to a common value scale (e.g., zero to one). Value functions for each attribute were constructed with subject-matter expertise assignment. In G-CBN-TP, the majority of the value functions are linear. In some cases however, some specific functions are exponential or logarithmic. The use of value functions allows the combination of attributes to be aggregated using value as the common yardstick.
Each attribute is uniquely weighted based on its impact on the overall potential threat for the country. SMEs are used to determine the weights where needed. A key advantage of the SMEs doing the weighting is that they are forced to see the trade-offs as they increase or decrease the weight of one criterion over another. SME reviewed published articles related to the criteria to help inform the decision process and discussed each criterion prior to defining the weights. Weights were assigned by consensus.
Once the weights are assessed, then the scores of countries on individual attributes are aggregated into a single priority score, summing the components that are additive and multiplying the components that are interdependent as described in detail below [6]. The G-CBN-TP model collects and analyzes data at a country-specific level. This data is used to score the attributes for each objective. The total weighted score of the attributes provides the Global Threat Priority score for the country that reflects its threat potential. This final score is then used to prioritize the modeled countries relative to each other. For each country, this model also allows for a detailed analysis of the threat drivers. This detailed analysis can be used in strategic planning at the country level and, over time, to demonstrate levels of threat reduction resulting from implemented projects.
To define the potential access of a country’s infrastructure to a nonstate actor, the following multiplicative value model was used (because the security culture of a country and the susceptibility of the country’s infrastructure are interdependent):
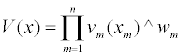
where the attribute measure, xm is the level of the mth attribute measure, vm(xm) is the value of the attribute value function at level xm, and wm is the weight associated with that attribute measure. To define the extent of a country’s infrastructure, and in defining the threat within a country, the following additive value model was used to combine all the infrastructure measures where the variable definitions are the same as in the previous equation.
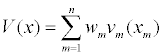
Conclusion
The G-CBN-TP model has provided a systematic prioritization of countries based the relative threat and vulnerability potential of each country. This model is currently being used by the US government in making strategic decisions regarding cooperative threat reduction activities and is being evaluated as a possible method to capture threat reduction metrics.
References
- Kirkwood CW (1997) Strategic Decision Making: Multiobjective Decision Analysis with Spreadsheets, Belmont, California: Duxbury Press, USA.
- Keefer D, Kirkwood CW, Corner JL (2007) Perspective on Decision Analysis Applications in: Edwards W, Miles R, von Winterfeldt D, eds. Advances in Decision Analysis, Cambridge, UK: Cambridge University Press, 154-176.
- Clemen RT, Reilly T (2004) Making Hard Decisions with Decision Tools Suite: Update Edition, Mason, OH: South-Western College Publishing, USA.
- Keeney R, Raiffa H (1993) Decisions with Multiple Objectives: Preferences and Value Tradeoffs, Cambridge, UK: Cambridge University Press, UK.
- Ewing, PL, Tarantion W, Parnell GS (2006) Use of Decision Analysis in the Army Base Realignment and Closure (BRAC) 2005: Military Value Analysis, Decision Analysis 3.
- Parnell GS, Jackson JA, Jones BL, Lehmkuhl LJ, Conley HW, et al. (1998) Foundations 2025: A Value Model for Evaluating Future Air and Space Forces, Management Sciences 44: 1336-1350.
Relevant Topics
- Anthrax Bioterrorism
- Bio surveilliance
- Biodefense
- Biohazards
- Biological Preparedness
- Biological Warfare
- Biological weapons
- Biorisk
- Bioterrorism
- Bioterrorism Agents
- Biothreat Agents
- Disease surveillance
- Emerging infectious disease
- Epidemiology of Breast Cancer
- Information Security
- Mass Prophylaxis
- Nuclear Terrorism
- Probabilistic risk assessment
- United States biological defense program
- Vaccines
Recommended Journals
Article Tools
Article Usage
- Total views: 15365
- [From(publication date):
December-2013 - Nov 22, 2025] - Breakdown by view type
- HTML page views : 10593
- PDF downloads : 4772